An information stealer, often referred to as an “infostealer” or simply a “stealer,” is a type of malware, designed to hide itself and secretly collect sensitive data. Its main objective is to extract information from any compromised computer.
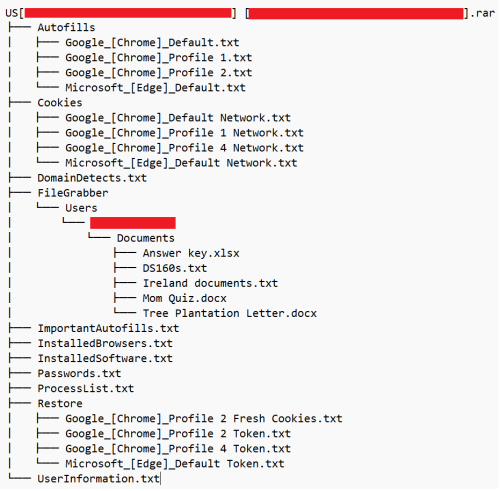
Infostealers are frequently sold in cybercriminal forums and Telegram groups. Unlike more complex malware that requires advanced skills to develop or deploy, infostealers are often sold with user-friendly interfaces, step-by-step guides, and even customer support. This means that even individuals with little to no technical knowledge can purchase and use these tools to carry out cybercrimes. As a result, the widespread availability of infostealers has expanded their use beyond seasoned hackers to include a broader range of criminals, increasing the overall threat landscape.
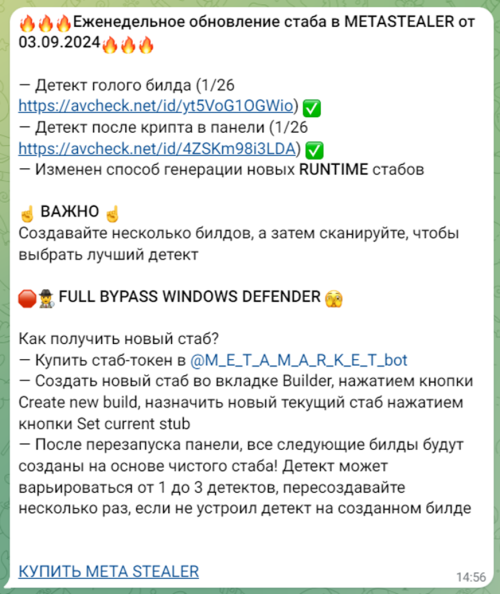
Information stolen by infostealer malware are sold in bulk on specialized markets called Credential Markets, on cybercrime forums and on Telegram groups. Every day, tens of thousands of logs end up for sale, and more are either leaked or published to advertise these channels. When sold, the price of a log usually ranges from $2 to 20. This huge mole of compromised, low-cost data constitutes a precious resource for opportunistic attackers, which regularly go through logs to collect credentials and authentication cookies that can be used to either launch an attack or re-sold to other threat actors.
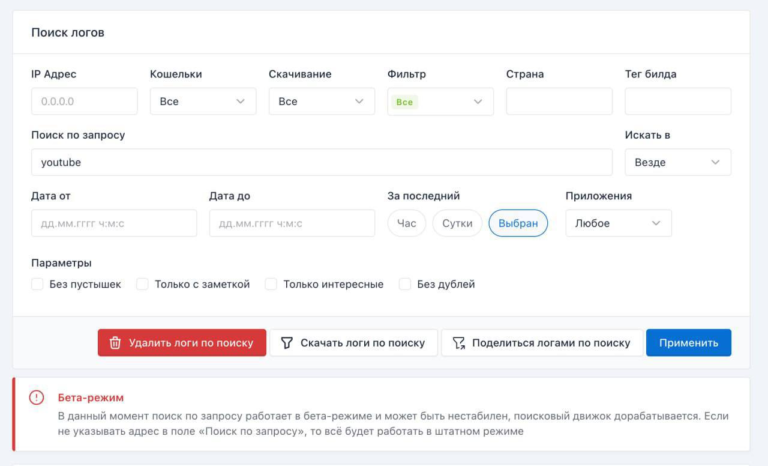
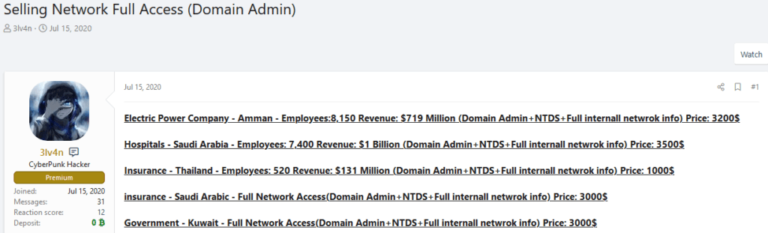
Access Brokers are threat actors which specialize in gaining access to medium to high value businesses, sometimes escalate privileges, and then re-sell the access to other criminals group such as Ransomware Gangs. Stealer logs represent a primary resource for Access Brokers, since it allows them to gain an initial foothold to a multitude of companies quickly and cheaply compared to other methods.
Infostealer malware represents a threat that cannot be handled with traditional methods. It can infect personal computers of employees, which the company has zero visibility on, or even devices owned by contractors. Security software would not block an access obtained with an infostealer, since it is a valid access with legitimate credentials. Multi-factor authentication, while useful, can be bypassed using valid authentication cookies gathered by a legitimate user infected with an infostealer. As a result, log distribution channels constitute a whole new hidden attack surface that cannot be patrolled using traditional security software. Over 50 million accounts where compromised by infostealers in the first half of 2023 alone. Most breach-detection services focus on public breaches and do not cover log distribution channels, leaving companies in the dark about the vast majority of compromised users and assets.
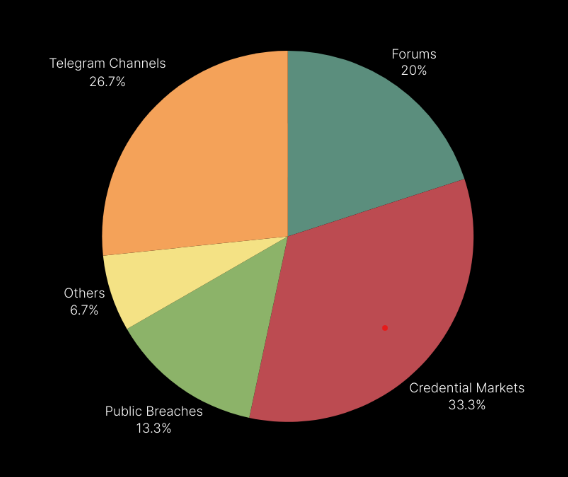
Delfi continuously scans log distribution channels, together with traditional sources, to immediately monitor our customers when their data are compromised. When a match is found between monitored keywords and domains and scraped data, an alert is generated with all the necessary information to remediate the threat before the stolen data are weaponized by threat actors to launch an attack.
This information includes:
Our platform can be configured in a few minutes, doesn’t need to be integrated in your infrastructure (but can if needed), and immediately provides you with infostealer and account takeover prevention coverage.
Do you want to learn more? Take a look at our product page or contact us to receive a free exposure report and a demo.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.