Background
Since 2023, the Rilide Infostealer has emerged as a growing threat in the landscape of information stealers. Primarily targeting browsers based on the Chromium engine, such as Google Chrome and Microsoft Edge, Rilide operates as a browser extension and can access login credentials, cookies, and even cryptocurrency wallets.
This article delves into an investigation of a Rilide sample distributed alongside a custom PowerShell loader to evade detection. The attacker’s custom code includes a mechanism to send an alert with system information to a Telegram channel whenever the loader is executed. Due to a permission misconfiguration, it was possible to access the channel, recover the full list of infected devices, and identified the Telegram account used by the threat actor to manage the channel.
Inspecting the loader
The PowerShell loader is divided into two stages. In the first stage, two constants are defined (“p94oc“, holding the AES-encrypted second stage, and “UG8Nu5“, holding the decryption key). The code is invoked using Invoke-Expression after being decrypted by the decrypt() function:
Set-Variable p94oc -Option Constant -Value 'qlzVmHUcEvt0o[...]'
Set-Variable UG8Nu5 -Option Constant -Value System.Text.Encoding]::UTF8.GetString(([byte[]] ( 87, 103, 47, [...] ))))
function decrypt( $UG8Nu5, $T7Ek )
{
$LV2q = [System.Convert]::FromBase64String( $T7Ek )
$irW2N = $LV2q[0..15]
$nTMr = createAesManagedObject $UG8Nu5 $irW2N
$ybXNa = $nTMr.CreateDecryptor()
$M5Tz = $ybXNa.TransformFinalBlock( $LV2q, 16, $LV2q.Length - 16 )
$nTMr.Dispose()
return [System.Text.Encoding]::UTF8.GetString( $M5Tz ).Trim( [char] 0 )
}
Invoke-Expression ( decrypt $UG8Nu5 $p94oc )The decrypted second stage subsequently executes the following actions:
- Gathers information about the current user, their privileges, the device, and the local groups present on it.
- Retrieves the device’s IP address and location by sending a GET request to “http://ipapi.com/json/?fields=status,message,query,country,regionName,city,isp,timezone”.
- Extracts the Rilide extension – stored in the second-stage itself – into a temporary folder, “C:\Users[user]\AppData\Roaming[random value]\”.
- Collects a list of installed Chromium-based browsers and installs the extension by manually copying files and modifying certain registry keys and security preference files of the browser .
- Deletes the temporary folder.
- Sends a report to the threat actor via a dedicated Telegram channel, including the information collected in the first point and a complete log of the installation. To allow this, the bot token and the id of the channel are included in the script.
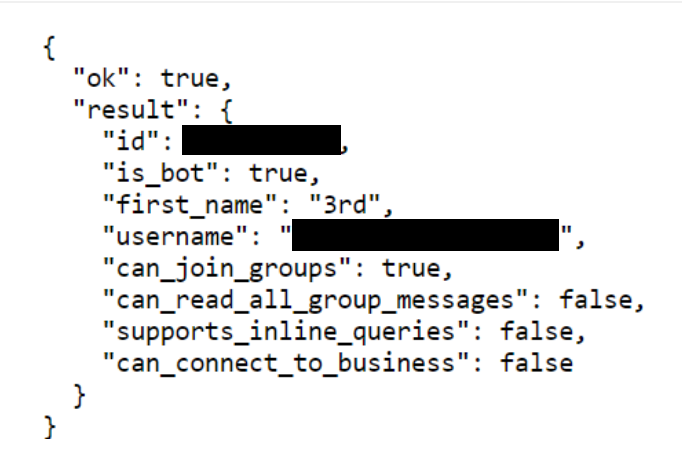
Typical behavior for an information stealer loader. During analysis, the bot token used to send messages to the Telegram channel was still active. This was verified by calling the Telegram API /getMe method via a GET request to “https://api.telegram.org/bot[BOT_ID]:[TOKEN]/getMe“.
The /getMe call returned basic information about the bot, such as its ID and username, confirming the token was still valid:
Accessing the channel
At the time of analysis, the channel used to send the messages was private, meaning only members could see its content. The Telegram Bot API offers a multitude of functionalities, but none to read messages from a channel. However, a few methods can be exploited to access the content if the channel is configured insecurely.
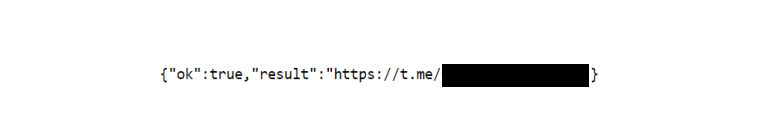
If the bot is an administrator of the channel and has the necessary permissions, the /createChatInviteLink method can be used to generate a link that allows any Telegram user to join the channel using a GET request to “https://api.telegram.org/bot[BOT_ID]:[BOT_TOKEN]/exportChatInviteLink?chat_id=[CHAT_ID]“.
This is not the case for most channels used by infostealers to receive updates. However, this time, upon calling /createChatInviteLink, the following response was returned:
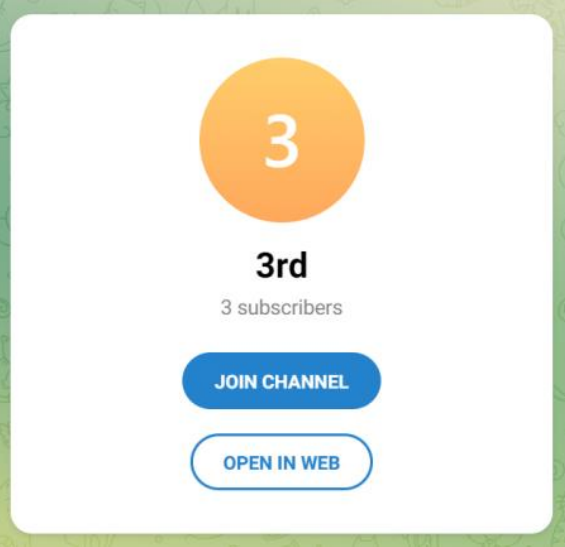
Opening the link allowed any user to join the channel, which had 3 subscribers at the time of analysis (including the bot):
The channel was active at the time of analysis, receiving dozens of new messages from infected devices daily. These messages contained a text attachment with an installation log of the malware, detailing environment data (such as the Active Directory domain name, malware installation path, and more), any errors encountered – likely for debugging purposes – and basic information about the newly infected system:
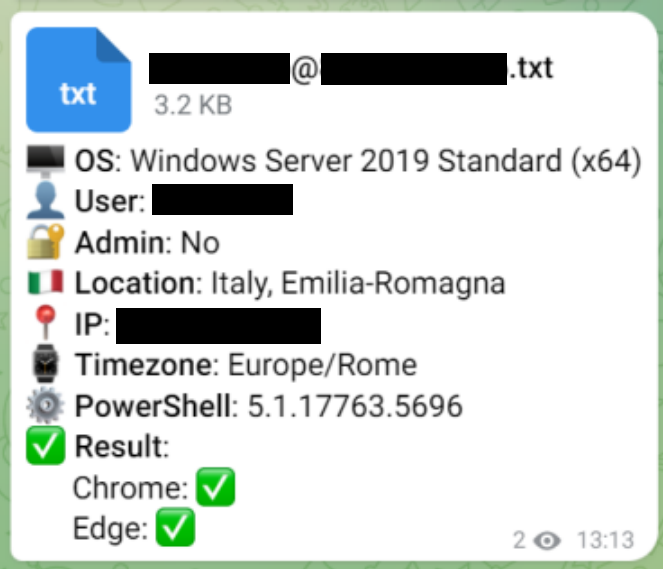
Scraping the channel allowed the discovery of 291 infected devices along with basic system information. Where identification was possible through the data in the installation log (mainly the Active Directory domain names), the affected parties were notified.
Identifying the Telegram account used to manage the channel
By using a GET request to “https://api.telegram.org/bot[BOT_ID]:[BOT_TOKEN]/getChatAdministrators?chat_id=[CHAT_ID]“, the account utilized by the threat actor to manage the channel was identified:
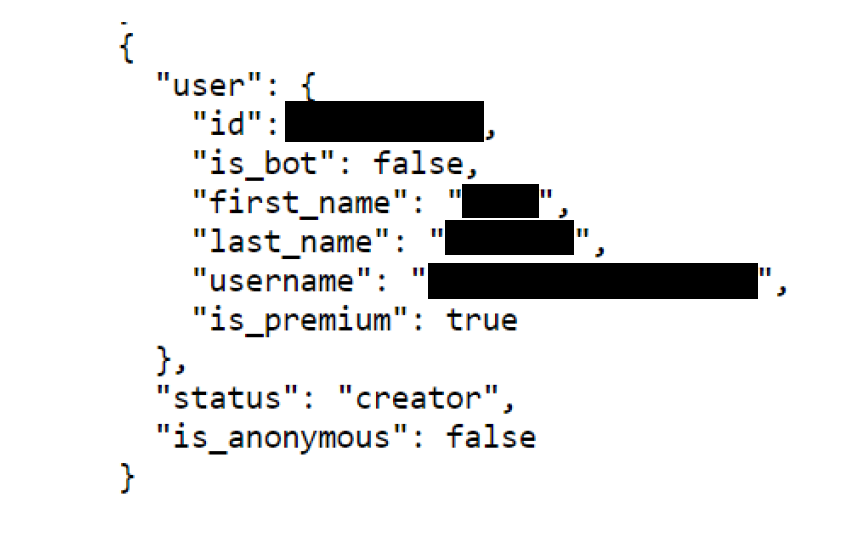
The account was still active at the time of analysis:
Although interesting information about Telegram accounts can sometimes be discovered if their privacy settings are misconfigured, this wasn’t the case. Therefore, the investigation into this account ceased here.
Conclusions
Telegram has been exploited by threat actors for years, and infostealer distributors are no exception. Using Telegram channels provides several advantages to attackers, such as not needing web hosting. However, misconfigured channels can offer incident responders crucial information, as it is always possible to extract the bot token and channel ID from the malware sample. It is also possible to flood the channel with fake data, making it unusable for the owner. In some cases, it is even possible to remove the owner or shut down the channel. Delfi Security believes that every incident responder would benefit from knowing how to assess the security of Telegram channels and applying that knowledge when dealing with malware samples using them for C&C or exfiltration.

